Configure-DKIM,SPF,DMARC-to-protect-against-spoofing: Difference between revisions
(Created page with "<big>Email Authentications prevent the email from going into the spam folder of recipients. cPanel uses DKIM and SPF to reduce the amount of spam mails. Enabling these features will prevent spammers from forging messages that claims to be coming from your domain.</big> <big>DKIM</big> <big>Domain Key Identification Mechanism (DKIM) verifies your incoming emails to check whether they are same as they were before when they were sent. This means, if they are altered durin...") |
(No difference)
|
Revision as of 06:45, 3 September 2025
Email Authentications prevent the email from going into the spam folder of recipients. cPanel uses DKIM and SPF to reduce the amount of spam mails. Enabling these features will prevent spammers from forging messages that claims to be coming from your domain.
DKIM
Domain Key Identification Mechanism (DKIM) verifies your incoming emails to check whether they are same as they were before when they were sent. This means, if they are altered during the transit. It also checks whether they are from the same address, whom they claim to be. This feature prevents incoming spam emails.
When DKIM is enabled, the sender signs the email with a digital signature using a private key. When the email approaches the recipient, it retrieves the public key of its sender and checks if the signature matches. If the signature is invalid, then message is treated as a spam message.
Enabling DKIM
To enable DKIM follow these steps −
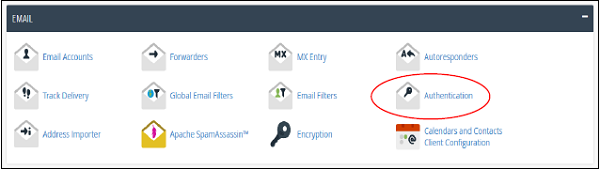
Step 1 − Open Email Authentication by clicking Authentication found under Mail Section of cPanel Home.
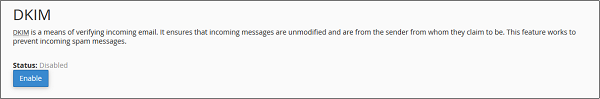
Step 2 − Find DKIM settings, if disabled then, click Enable button to Enable DKIM.
Disable DKIM
To disable DKIM follow these steps −
Step 1 − Open Email Authentication by clicking Authentication found under Mail Section of cPanel Home.
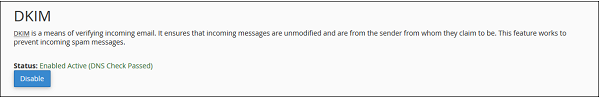
Step 2 − Find DKIM setting, if enabled, then click Disable button to Disable DKIM.
Note − To Enable DKIM, your Nameservers must point to your hosting. It is recommended that you use DKIM Authentication in your hosting.
Advertisement
SPF
Sender Policy Framework (SPF) helps in preventing outgoing messages to spams. This helps to prevent spammers in creating a message that looks like it is originated through your domain. SPF uses TXT type DNS resource records, which specify the hosts that send emails through your domain.
Enable SPF
To enable SPF, follow these steps −
Step 1 − Open Email Authentication by clicking Authentication found under Mail Section of cPanel Home.
Step 2 − Find SPF setting, if disabled, then click Enable button to Enable SPF.
Disable SPF
To disable SPF, follow these steps −
Step 1 − Open Email Authentication by clicking Authentication found under Mail Section of cPanel Home.
Step 2 − Find SPF setting, if enabled, then click Disable button to disable SPF.
DMARC (Domain-based Message Authentication, Reporting, and Conformance)
DMARC builds upon SPF and DKIM by:
- Providing clear policies for handling authentication failures
- Enabling domain owners to receive detailed feedback reports about email authentication
- Creating alignment between the various sender identities in an email
- Allowing for progressive implementation through graduated enforcement policies
How DMARC Works
DMARC operates through a DNS TXT record that instructs receiving mail servers how to handle emails that fail authentication. The process works as follows:
- The sending domain publishes a DMARC policy in its DNS records
- When an email arrives, the receiving server checks for SPF and DKIM authentication
- The receiving server verifies "alignment" between the authenticated domain and the visible From: domain
- Based on the published DMARC policy, the receiver takes appropriate action (none, quarantine, or reject)
- The receiver generates reports and sends them back to the address specified in the DMARC record
DMARC Policies
DMARC offers three policy options of increasing strictness:
- p=none: Monitor mode that requests reports but takes no action against failing messages
- p=quarantine: Suggests that failing messages should be placed in spam or junk folders
- p=reject: Instructs receivers to block failing messages entirely
Implementing DMARC: A Step-by-Step Approach
1. Assessment and Planning
- Identify all legitimate sources of email from your domain
- Map out your email infrastructure
- Determine which third parties send email on your behalf
- Set goals and timelines for DMARC implementation
2. Implement SPF
- Create an SPF record listing all authorized sending servers
- Publish the SPF record in your DNS
- Test to ensure legitimate emails are passing
- Example SPF record: v=spf1 ip4:192.0.2.0/24 include:_spf.example.com -all
3. Implement DKIM
- Generate DKIM key pairs
- Configure your mail servers to sign outgoing messages
- Publish your DKIM public keys in DNS
- Verify signatures are being applied correctly
4. Deploy DMARC in Monitoring Mode
- Start with a "p=none" policy to gather data without affecting mail flow
- Publish a basic DMARC record: v=DMARC1; p=none; rua=mailto:dmarc-reports@example.com
- Analyze the resulting reports to identify legitimate sources that may be failing authentication
5. Coordinate with Third-Party Senders
- Share your DMARC implementation plans with authorized third parties
- Help them configure proper authentication for your domain
- Consider implementing subdomain delegation where appropriate
6. Gradually Increase Enforcement
- Move to "p=quarantine" with a percentage tag once monitoring shows minimal false positives
- Example: v=DMARC1; p=quarantine; pct=25; rua=mailto:dmarc-reports@example.com
- Gradually increase the percentage to 100%
7. Move to Full Rejection
- Once confident in your authentication coverage, implement "p=reject"
- Example: v=DMARC1; p=reject; rua=mailto:dmarc-reports@example.com; ruf=mailto:forensic@example.com
- Continue monitoring reports for unexpected failures